WE HAVE A LOT TO SAY
IT SOFTWARE APPS CLOUD NEWS EVENTS
LIVE 24/7 SUPPORT (646) 461-1698
Blog
Stay up to date with technology services

What Are Smart Contracts and How Can They Enhance Your Company’s Security
What Are Smart Contracts and How Can They Enhance Your Company's Security? Smart contracts are making some significant upgrades to existing supply chains and digital business transactions happening worldwide. They allow you to conduct secure and accurate transactions of any kind from bill payments, sale agreements, data transfers, and more across the globe. They have proven quite helpful in enhancing your company's security, preventing fraudulent transactions and errors in your...

Accounting in the Clouds: Why You Should Host Your Quickbooks Software Online?
Accounting in the Clouds: Why You Should Host Your QuickBooks Software Online? QuickBooks is a financial management and accounting software that has been a favorite among businesses of all sizes. With over 4.5 million active users worldwide, QuickBooks comes with three different pricing plans and a trial period. It is easy to use, packs in powerful accounting features and is affordable and easy to master for small businesses. However, there is one Quickbooks offering that is...

What Is a Network Security Key and Where to Find It
What Is a Network Security Key and Where to Find It If you are looking for a network security key, you are more than likely to be in the process of trying to connect a new device to your home or workplace Wi-Fi network. Or, perhaps, you are trying to reconnect an existing device after a system update or a router reset. In any case, you need to know your network security key to continue business as usual. Network security key is, essentially, a password on steroids...
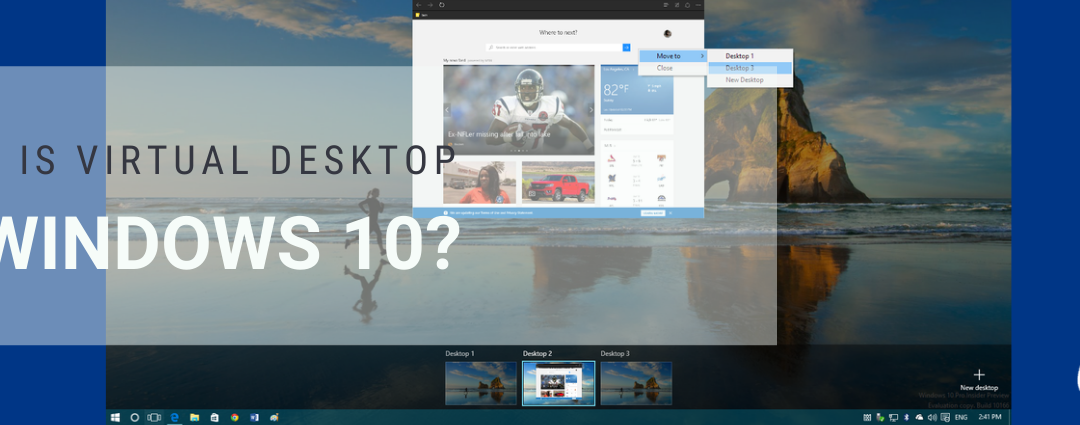
What Is Virtual Desktop in Windows 10?
What Is a Virtual Desktop In Windows 10? Thanks to the October 2020 update, Windows 10 has made it extremely easy and convenient to set up and use multiple virtual desktops in Windows 10. Multiple virtual desktops are a respite to keep all the chaos at bay, reduce information overload, organize the existing projects, and, if we are being honest, quickly hide an occasional Youtube video from the boss. In other words, a virtual desktop in Windows 10 is a tool to organize...

Cloud Computing Is Growing. Here Is Why Cloud Technology Is the Future.
Cloud Computing Is Growing and Here Is Why Cloud Technology Is the Future In general, cloud computing refers to the on-demand delivery of services over the internet (or ‘cloud’), including software, data storage, or processing services. Through cloud computing, you can access these IT services without the need to maintain physical data centers or servers. Additionally, you only need to pay for the cloud services you use, rather than cashing out a much larger sum for setup and...

Windows 11 Update: What’s New and What to Know
Windows 11 Update: What’s New and What to Know The much-awaited Windows 11 is set to officially release on October 2021, and its beta version is already out, available only for users who are part of the Windows Insider program. Ever since the announcement from Microsoft back in June, there has been quite a buzz around the latest version of the Windows OS. So with the beta version available and the official release date approaching fast, here’s everything you need to know...

Malware-as-a-Service: How to Keep Your Business Safe
Malware-as-a-Service: How to Keep Your Business Safe You have probably heard of—and most likely used—at least one technology solution delivered through the Software-as-a-Service (SaaS) model. SaaS means that the service “lives” in the cloud instead of your company’s servers, and all you need to do is “plug into” the cloud to use it. SaaS usually has an associated subscription fee which is how SaaS providers earn their revenue. Ease of access, lower cost, endless scalability,...

Outsource vs Insource: Pros and Cons
Outsource vs Insource: Pros and Cons Outsourcing started with back office and admin functions and then gradually spread into other niches like manufacturing, IT, and software development. IT outsourcing is rather popular these days, considering that the global IT market will touch $481.37 billion by 2022, growing at a CAGR of 6.2%. Although outsourcing is getting popular, insourcing is still what most companies stick to. Insourcing involves the practice of hiring an employee...

What Do IT Managed Services Companies Do?
What Do IT Managed Services Companies Do? Whatever the size of your business, small, big, or mid-level, you will need the help of IT services to run your day-to-day operations. In the increasingly digitized business world, every company needs a solid IT infrastructure to meet its operational requirements. But IT talent is expensive and not every company can afford to payroll a state-of-the-art IT department. Running an IT team takes a lot of investment, time, expertise, and...

What Is a Disaster Recovery Test and Why You Should Care?
What Is a Disaster Recovery Test and Why Should You Care? Stephen King said it: “There's no harm in hoping for the best as long as you're prepared for the worst.” With 2,244 cyber attacks happening every day—that is one attack every 39 seconds somewhere on the Internet!—there is no guarantee that your business will be overlooked by the hustling hackers. Cybersecurity has three pillars: Prevention Mitigation Recovery The latter step—Recovery—is most frequently...
