WE HAVE A LOT TO SAY
IT SOFTWARE APPS CLOUD NEWS EVENTS
Your Next Phishing Email May Be From Microsoft — Here Is What You Should Look Out For
More and more businesses migrated to Microsoft Office 365 in 2020, and hackers took notice. The changing work environment contributed to Microsoft Teams reaching 115 million daily active users in October 2020, a 50% surge in just six months. Microsoft Outlook remains the preferred business email client for many organizations. And Microsoft Azure is in the top-3 most popular cloud platforms.
It doesn’t come as a surprise, then, that the “Microsoft look” is en vogue with the hackers: recently it has been reported that 45% of phishing emails were Microsoft-themed.
What does a Microsoft phishing lure look like?
Malware statistics indicate that credential-stealing phishing attacks impersonating Microsoft tend to take one of the three popular “notification” formats:
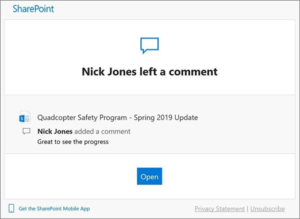
‘Pam wants to share a document with you.’
This standard Sharepoint notification is pure gold for anyone craving your staff’s Microsoft credentials. The unsuspecting user will click the button to “view the document,” will be asked to sign in, and their credentials will land directly in the hackers’ hands.
Source: Microsoft
It is worth noting that while Microsoft takes the lead in the number of attacks impersonating the brand, criminals don’t shy away from other cloud hosting services such as Dropbox, Box, Adobe, Google Drive, WeTransfer and DocuSign.
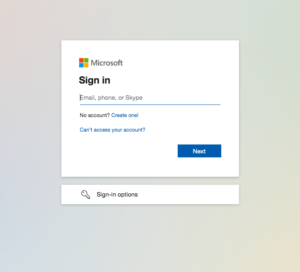
‘Sign into your account.’
Sometimes, hackers don’t bother with storytelling and simply send an email with a link instructing users to sign into their Office 365 account. Clicking the link in the email takes the user to a webpage made to look very similar to the original sign in page.
Source: Microsoft
The best mitigation strategy in this case would be to check if you are still signed into your services outside of email, such as, are you still able to access Microsoft Teams? If you are, report the suspicious email immediately and avoid clicking on the links. If the link is clicked, make sure that the URL is correct—doesn’t contain extra letters or numbers, isn’t misspelled, or unrelated to Microsoft—before entering any data.
Attachments
Attachments are another wide-spread form of phishing. Usually an attached pdf will require a sign in to Microsoft OneNote or OneDrive to view. Sometimes the email may contain a link to download the document instead, as is the case with the popular “TRANSFER OF PAYMENT NOTICE FOR INVOICE” leading busy accountants to “download” non-existing invoices from the web.
More often than not, hackers will host these files and sign in pages on legitimate servers, making it harder for anti virus software and firewalls to track them. Advanced security solutions, such as Endpoint Detection and Response, have a higher chance of catching malicious emails before it’s too late.
Protecting Your Business Against Microsoft Scams
If your team doesn’t use Office 365, or any other software that seems to be sending you emails, the easiest way to minimize the risk is to delete the email immediately. For instance, if you routinely use Zoom but receive a sign in request for Microsoft Teams, it may be wise to check with your IT department first before engaging with it. However, if your business runs on Microsoft software as many businesses do, it may be hard to distinguish authentic email notifications from malicious ones.
Educating your team and setting up comprehensive email security protocols are the two main steps in minimizing the chance of a successful attack. A good place to start may be these two blog posts: 3nom’s Ultimate Guide to Email Security for Your Business and Email Security Protocol Template for Small and Medium-Sized Businesses. And for a comprehensive free security training for your entire team, check out our Security Awareness training.